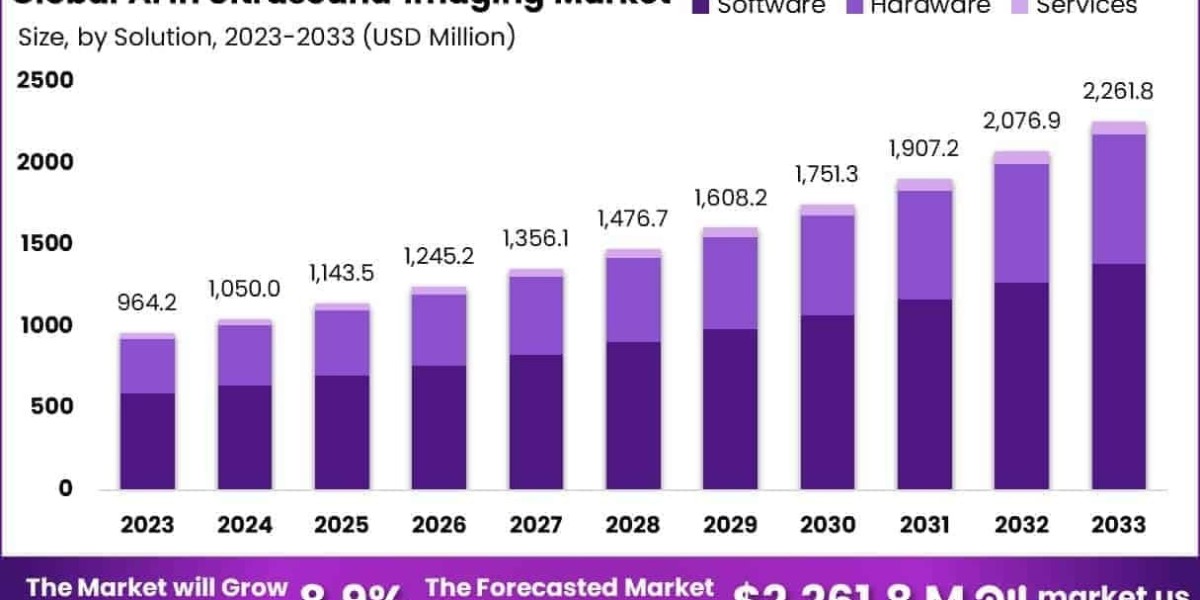
The Global AI in Ultrasound Imaging Market size is expected to be worth around USD 2261.8 Million by 2033, from USD 964.2 Million in 2023, growing at a CAGR of 8.9% during the forecast period from 2024 to 2033.
In 2025, the AI in Ultrasound Imaging Market is transforming clinical ultrasound with real-time analytics and workflow automation. AI-enabled systems are now capable of auto-detecting anomalies (e.g., nodules, cardiovascular markers) during live scans, assisting sonographers instantly. Automated measurement tools like ejection fraction or fetal biometry reduce manual variability and speed reporting.
This integration is reducing scan time by up to 30% and improving diagnostic consistency. Major ultrasound OEMs are licensing AI modules from startups, while hospitals invest in subscription-based AI platforms. With growing evidence of cost savings and improved patient outcomes, AI-assisted ultrasound is becoming a standard feature in both high-end and point-of-care systems.
Click here for more information: https://market.us/report/ai-in-ultrasound-imaging-market/
Emerging Trends
- Live anomaly detection during scanning, enabling immediate follow-up.
- Automated biometric measurements, such as cardiac ejection fraction and fetal growth.
- AI-powered scan guidance, encouraging standardized image capture even by novices.
- Subscription AI modules incorporated into OEM platforms for scalable deployment.
Use Cases
- A cardiology unit uses AI to auto-calculate ejection fraction mid-scan, allowing instant diagnosis during consultations.
- Prenatal clinics deploy fetal measurement AI that flags biometric outliers, improving accuracy across centers.
- Emergency department staff use scan guidance AI to ensure consistent FAST exam coverage.
- A mobile ultrasound cart in rural clinics uses plug-and-play AI modules to support community sonographers.