Trezor.io/Start and Trezor Login – Your Complete Guide to Secure Crypto Access
The world of cryptocurrency continues to expand at a rapid pace, and with it comes the growing need for strong security. For investors and traders alike, safeguarding digital assets is no longer optional but essential. This is where Trezor, one of the most trusted hardware wallet providers, comes into the picture. If you have purchased a Trezor device or are planning to set one up, the journey begins at Trezor.io/Start. From there, you will also need to understand the importance of the Trezor login process to ensure smooth access to your crypto funds.
Getting Started with Trezor.io/Start
Trezor.io/Start is the official setup page for new users. When you unbox your Trezor device, whether it is the Trezor Model One or the Trezor Model T, this page serves as the safe and reliable starting point. It provides step-by-step guidance for installing Trezor Suite, updating firmware, and creating your wallet. By starting here, you guarantee that you are working with official software and not a third-party application that could compromise your security.
Once you connect your device to your computer, the page will guide you to download Trezor Login, which is the application you will use to manage your assets. Trezor Suite is available for both desktop and web, but most users prefer the desktop version because it reduces potential risks associated with browser vulnerabilities.
During setup, you may also be prompted to update your device firmware. Firmware updates are critical because they not only add new features but also patch potential security issues. Keeping your device up to date ensures that your wallet is operating with the latest protections.
Creating Your Trezor Wallet
After installing Trezor Suite, the next step is generating your wallet. When you create a new wallet, the device will generate a recovery seed consisting of 12, 18, or 24 words. This seed phrase is the foundation of your wallet security. It must be written down carefully and stored offline in a secure location. Trezor will never ask you to type your recovery seed into a computer or share it online. If anyone ever requests your seed phrase, it is a scam attempt.
The recovery seed ensures that even if your device is lost, stolen, or damaged, you can still recover your funds on a new device. Many users take extra precautions by using metal seed storage options to protect against fire, water, or physical damage.
Setting PIN and Passphrase Protection
Alongside your recovery seed, you will create a personal PIN code for the device. The PIN acts as the first line of defense if someone physically obtains your Trezor. Each time you connect the device, you will need to enter your PIN before making transactions.
For those who want enhanced protection, Trezor also offers the option to use a passphrase. This functions like an extra word added to your recovery seed, creating what is essentially a hidden wallet. Even if someone somehow discovers your recovery seed, without the passphrase, they will not be able to access your funds.
Understanding the Trezor Login Process
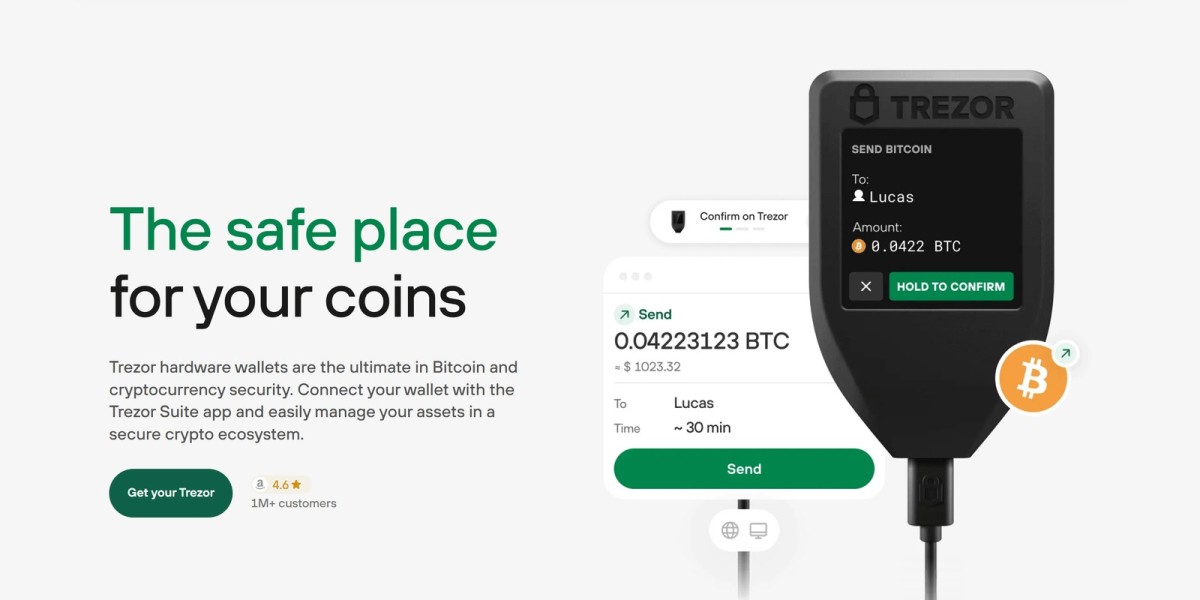
Once your device is set up, the next key step is understanding how the login process works. Trezor login is not the same as logging into a typical website with a username and password. Instead, it is a secure authentication process designed to keep your private keys offline at all times.
When you open Trezor Suite and connect your hardware wallet, you will be prompted to unlock the device using your PIN. This is followed by optional passphrase entry if you have enabled that feature. Importantly, all confirmations of transactions, addresses, or logins are displayed directly on the Trezor device screen. This means that even if your computer were infected with malware, you would still need to confirm the action physically on your hardware wallet.
This design ensures that your private keys never leave the device, reducing the risk of exposure to hackers. In simple terms, the Trezor login process is about verifying that the rightful owner is physically present and approving actions.
Using Trezor Suite for Daily Management
After login, Trezor Suite becomes your central hub for managing assets. You can view balances, generate new receiving addresses, send transactions, and monitor your portfolio. Every outgoing transaction must be confirmed on the device itself, which prevents unauthorized transfers.
The login process also extends beyond just Trezor Suite. Many third-party services and decentralized applications integrate with Trezor as a login method. Instead of creating accounts with passwords, you can use your Trezor device as a secure authentication tool, adding another layer of safety when interacting with blockchain applications.
Maintaining Security Beyond Login
While Trezor provides industry-leading hardware protection, users must still practice good security habits. Always ensure that you are downloading updates directly through Trezor Suite. Avoid storing your recovery seed digitally, and never share it with anyone. Be mindful when connecting your device to different computers, and avoid using it in unsafe environments such as public internet cafes.
The login process itself is highly secure, but its effectiveness depends on your personal responsibility. Treat your device as you would treat a bank vault key. If handled carefully, your assets remain safe no matter what threats may emerge online.
Final Thoughts
Starting with Trezor.io/Start and understanding the Trezor login process are essential steps in securing your cryptocurrency. The setup phase introduces you to Trezor Suite, firmware updates, recovery seeds, and PIN protection, while the login process ensures your private keys never leave your hardware wallet. Together, they form a security system that balances usability with protection.