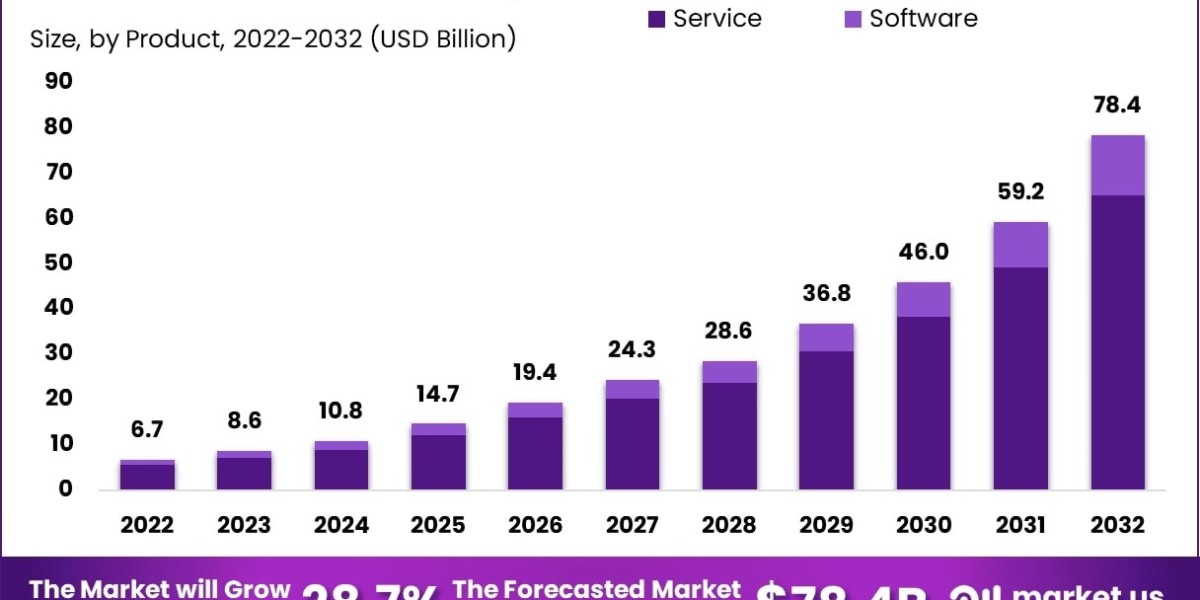
In the digital age, cybersecurity is a critical concern for businesses worldwide. As cyber threats become increasingly sophisticated, companies must prioritize safeguarding their data, systems, and reputation. Effective cybersecurity measures not only protect against potential attacks but also ensure business continuity and customer trust.
Understanding Cybersecurity
Cybersecurity encompasses strategies, technologies, and practices designed to protect networks, devices, programs, and data from unauthorized access, damage, or attacks. It involves a proactive approach to identifying and mitigating vulnerabilities within an organization's IT infrastructure.
Types of Cybersecurity Services
Businesses can leverage various cybersecurity services to fortify their defenses against evolving threats:
1. Network Security
Network security focuses on protecting an organization’s internal networks from breaches and attacks. It includes firewalls, intrusion detection systems, and secure network architecture.
2. Endpoint Security
Endpoint security involves securing devices such as computers, smartphones, and tablets that connect to a network. Advanced antivirus software, encryption, and mobile device management tools are common solutions.
3. Application Security
Ensuring that applications are secure during development and deployment helps prevent vulnerabilities that could be exploited by attackers. This includes implementing secure coding practices and regular application testing.
4. Data Security
Protecting sensitive data from theft, loss, or corruption is crucial. Data encryption, secure backups, and access control measures are key components of data security.
5. Cloud Security
As businesses migrate to cloud platforms, securing these environments becomes essential. Cloud security involves protecting data, applications, and services hosted in the cloud through encryption, identity management, and regular audits.
6. Identity and Access Management (IAM)
IAM ensures that only authorized users have access to specific systems and data. Multi-factor authentication (MFA) and role-based access controls are common IAM solutions.
Benefits of Implementing Robust Cybersecurity Measures
1. Protection Against Cyber Threats
Effective cybersecurity measures safeguard businesses from malware, phishing attacks, ransomware, and other threats.
2. Regulatory Compliance
Adhering to cybersecurity regulations and standards helps businesses avoid legal penalties and maintain industry certifications.
3. Enhanced Customer Trust
A strong security posture reassures customers that their data is safe, fostering trust and loyalty.
4. Business Continuity
By minimizing the risk of downtime and data loss, cybersecurity measures ensure uninterrupted operations.
5. Cost Savings
Preventing cyber incidents reduces the financial impact of breaches, including costs related to recovery, fines, and reputational damage.
Key Components of a Cybersecurity Strategy
Risk Assessment: Identify potential threats and vulnerabilities within the organization’s IT environment.
Incident Response Plan: Develop a clear plan to detect, respond to, and recover from cyber incidents.
Employee Training: Educate employees on best practices, such as recognizing phishing attempts and using strong passwords.
Regular Updates and Patch Management: Ensure that all systems and software are up to date to address known vulnerabilities.
Continuous Monitoring: Use advanced tools to monitor networks and systems for suspicious activity in real-time.
Emerging Trends in Cybersecurity
AI-Powered Security: Artificial intelligence and machine learning are enhancing threat detection and response capabilities.
Zero Trust Architecture: This model emphasizes verifying every user and device, regardless of location, before granting access.
Blockchain Security: Blockchain technology is being used to secure transactions and data sharing across decentralized networks.
IoT Security: As IoT devices proliferate, securing these endpoints is becoming a top priority for organizations.
Real-World Applications of Cybersecurity
1. Financial Sector
Banks and financial institutions implement advanced cybersecurity measures to protect sensitive customer data and prevent fraud.
2. Healthcare
Hospitals and healthcare providers secure electronic medical records (EMRs) and ensure compliance with privacy regulations.
3. Retail
Retailers protect point-of-sale systems and customer payment information from breaches.
4. Government
Government agencies employ cybersecurity to safeguard critical infrastructure and sensitive information.
Steps to Strengthen Cybersecurity
Conduct regular risk assessments to identify vulnerabilities.
Invest in advanced security tools and technologies.
Develop a comprehensive incident response plan.
Partner with cybersecurity experts for ongoing support and consultation.
Stay informed about the latest cyber threats and trends.
Conclusion
Cybersecurity is an indispensable aspect of modern business operations. By implementing robust security measures, organizations can protect themselves from potential threats, ensure business continuity, and build trust with their stakeholders. Businesses in Dubai and beyond must prioritize cybersecurity as an essential investment in their long-term success.